Who Would Be Interested?
Many different groups might be interested in using this tracking technology, each for their own purposes:
Marketing and advertising companies could use this to track consumer movement patterns without having to install expensive tracking equipment in stores. By understanding where people go and how much time they spend in different locations, they can create more targeted advertising campaigns.
Shopping apps and social media platforms might use this technology to track users' locations without explicitly asking for GPS permission. They could learn where you shop, what restaurants you visit, and other habits to send you personalized recommendations and ads. This data becomes extremely valuable when combined with your online browsing and purchasing history.
Data brokers and analytics firms collect and sell information about consumers. This tracking method would give them another source of valuable location data to enhance their profiles about individuals, which they then sell to other businesses, political campaigns, or anyone willing to pay.
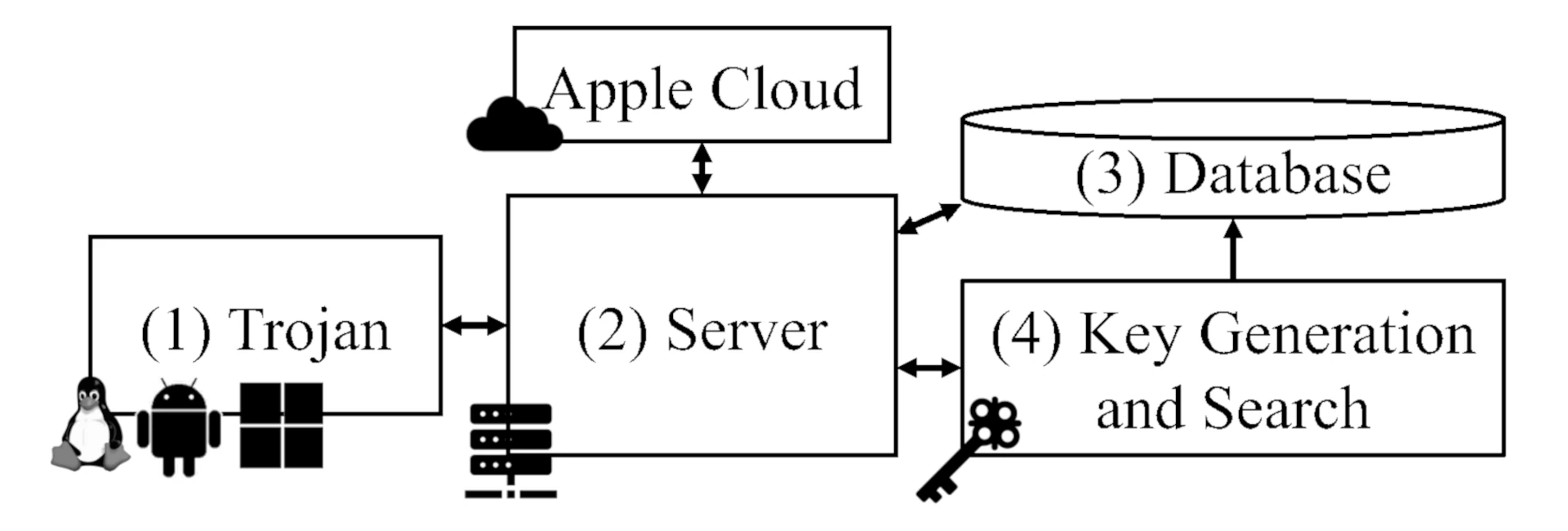
Government intelligence and law enforcement agencies might be interested in this technology for surveillance purposes. They could potentially track specific individuals by getting them to install software containing this tracking code. Unlike traditional tracking methods, this approach wouldn't require physical trackers or direct access to cell tower data.
Hackers and cybercriminals could use this tracking to identify when valuable devices are away from secure locations or to determine when people aren't home. This information could help them plan more effective device thefts or home break-ins. The method is particularly attractive because it's difficult to detect and doesn't require expensive equipment.
Stalkers and people with harmful intent might use this technology to track specific individuals. Unlike physical trackers that might be discovered, this software-based approach is virtually undetectable to the average person.